I Woke up and Everything Was Gone
Joe woke up to the buzzing of his phone and a hundred texts.
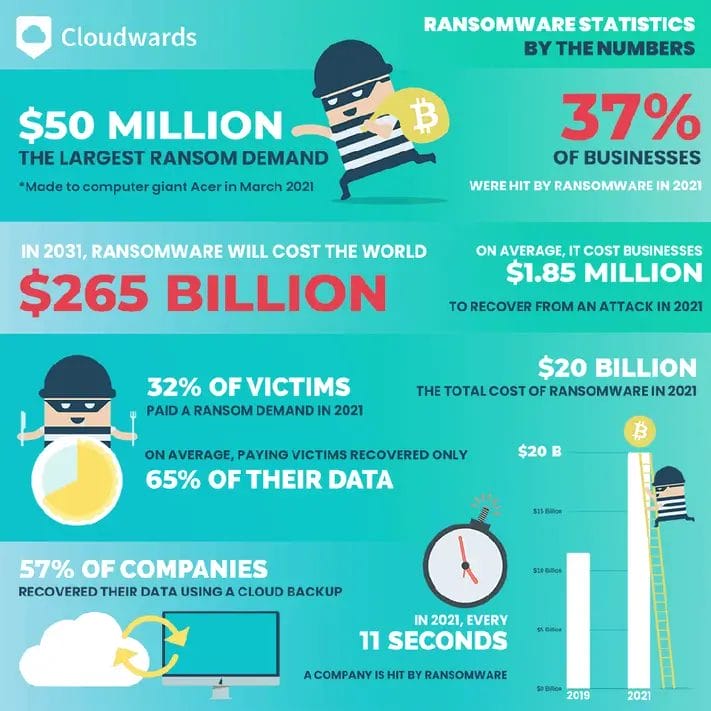
“Everything is gone”
Their CRM database was corrupted. His domain controller wouldn’t boot and all his files and computers were locked with a ransomware message.
It’s frightening how often this happens
The sad part is that most businesses have no plan in place for this inevitability
When Joe called us and told us what was going on, our techs got into action and reviewed their recovery policy and immediately got to work
We knew in what order things needed to be recovered and where and how to recover their systems
We informed Joe that our timeline was around 24 hours and set about recovering their servers and data in the order outlined by the disaster recovery plan we had updated only 8 months ago
We informed Joe that while this hack is frightening, we will get them back online and we can discuss with their cyber insurance company any fallout that may occur because of data getting leaked.
Even with top-end advanced endpoint protection, server protection, SAAS monitoring and employee training these types of situations can never fully be stopped
With our plan in place, we promptly got them back online and addressed the fallout with the organization’s top members and their insurance company
They were back online in our estimated 24-hour timeframe
If we hadn’t created a disaster recovery and cyber resiliency plan this could have gone a lot worse
Even if you have a cyber insurance policy, insurance companies often find ways to refuse pay out on claims if companies have not proven that they have done a sufficient job in their cybersecurity implementation, policies, and employee training
Joe could have been left rebuilding everything from scratch been stuck having a hard conversation with his clients (not to mention the loss of clients and the legal ramifications of client data being stolen)
Hacks are inevitable, hackers target businesses of all sizes and simply saying that hackers can have your data “because we don’t have anything important” will not protect you with the new FTC Safeguards that have been put in place.




