LME Services IT Blog
How to Stop Outlook From Automatically Creating Microsoft Teams Meetings
Why Outlook Automatically Creates a Microsoft Teams Meeting (And How to Stop It) If you’ve ever tried to create a simple calendar event in Outlook—only to find that Microsoft automatically turns it … Read more
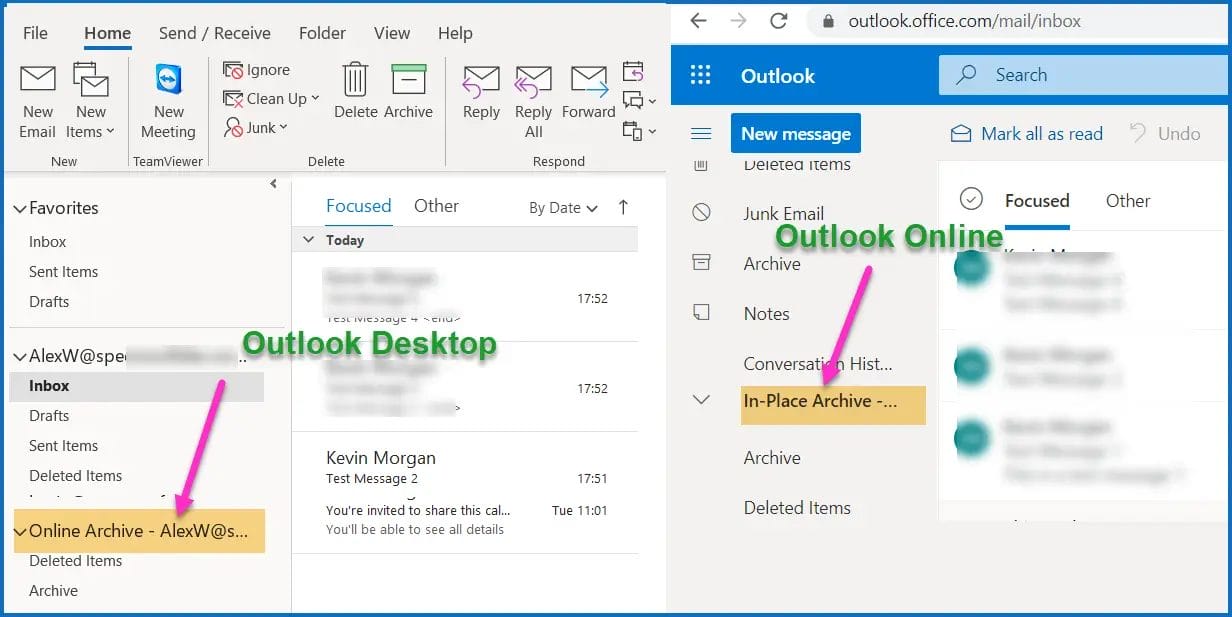
How to Automatically Archive Office 365 Email
How to Properly Set Up Auto-Expanding Archives in Office 365 (Step-by-Step Guide) Managing large mailboxes in Office 365 (now Microsoft 365) can be a major challenge for IT admins. Fortunately, auto-expanding archive … Read more
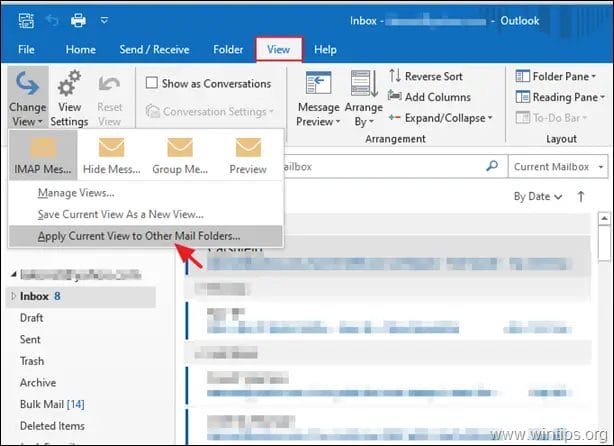
Gmail Emails Are Hidden or Missing
🛠️ Fix Missing Gmail Emails in Outlook After Migration or Move (IMAP Issue) If you use Outlook to access your Gmail account via IMAP or recently migrated emails or setup an Outlook … Read more

How to Fix Microphone Lag on Zoom
How to Fix Microphone Lag on Zoom – A Quick Troubleshooting Guide If you’re dealing with microphone lag on Zoom here is a guide that provides some of the most common fixes … Read more

Ai Assessment Services For Law Firms
AI Services for Law Firms | LME Services AI Services for Law Firms Automate. Analyze. Accelerate. All with full compliance and confidentiality. Tailored AI Solutions for Legal Professionals As a law firm, … Read more

How to Fix When You Can’t Switch Organizations in Microsoft Teams
Having Trouble Switching Organizations in Microsoft Teams? Here is how to fix it Microsoft Teams makes it easy to collaborate across multiple organizations—when it works. As many reddit users have discovered, sometimes … Read more
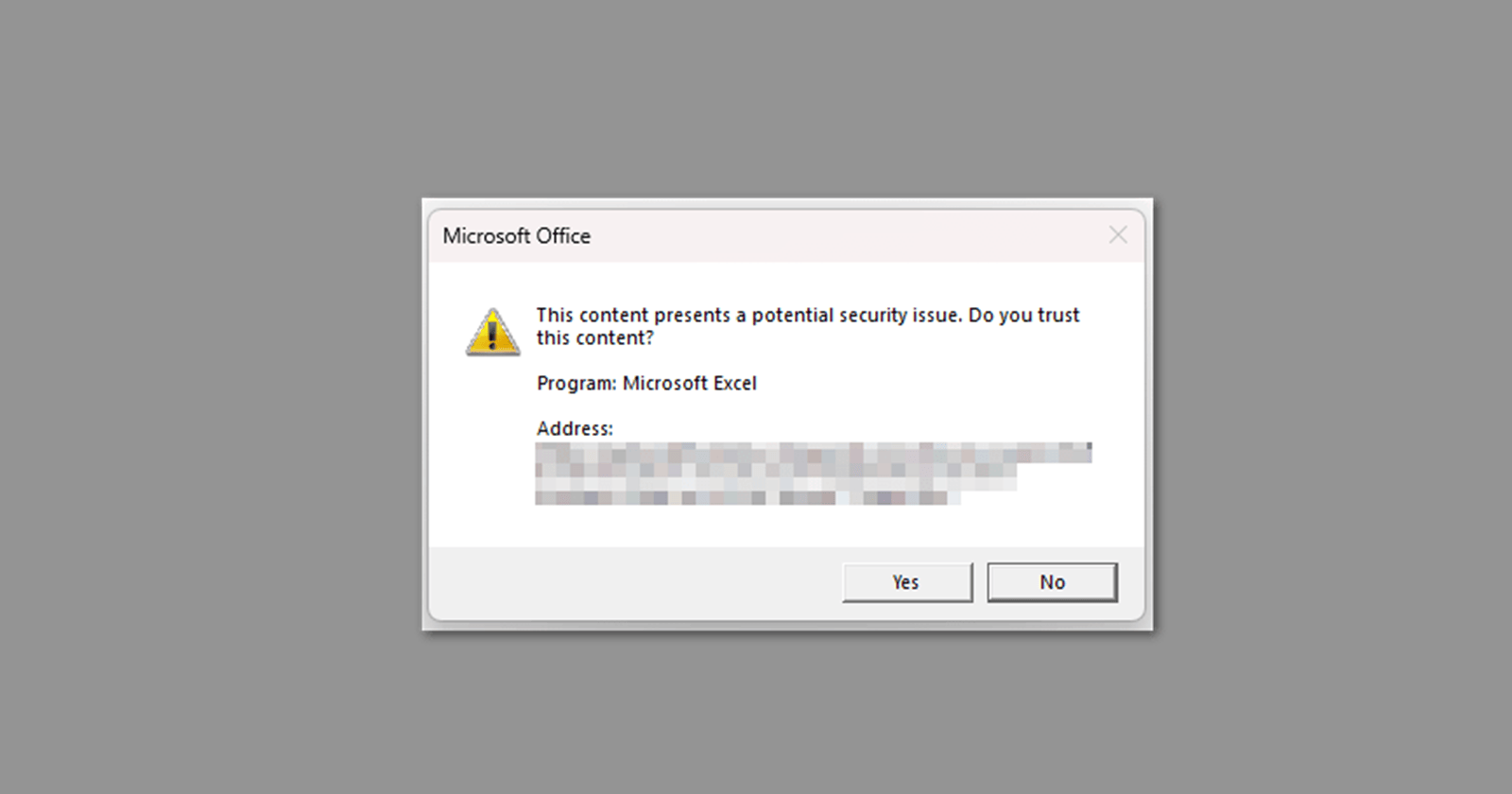
How to Fix the Excel Error: “This content presents a potential security issue. Do you trust this content?”
How to Fix the Excel Error: “This content presents a potential security issue. Do you trust this content?” Here is how to fix the Excel error message “This content presents a potential … Read more

How To Fix When O365 Outlook Doesn’t Display All Gmail Emails
Outlook Not Showing All Emails, But Gmail Does? Here’s How to Fix It Here is how to fix and when you are seeing emails in Gmail but they are missing emails in … Read more
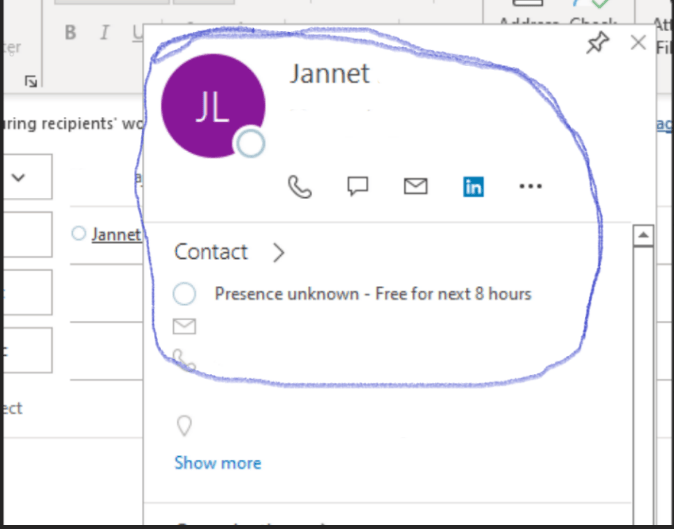
How to Fix Outlook 365 Not Showing Teams Presence Status
How to Fix Outlook 365 Not Showing Teams Presence Status Here is how to fix when Outlook 365 isn’t showing Teams presence status, like Available, Busy, or In a Meeting. Many reddit … Read more

Outlook Only Works in the New Version? Here’s How to Switch Back to Classic (If You Still Can)
How to Switch From New Outlook Back to Classic Outlook Have you noticed that Outlook only opens in the “new version”, here is how to switch from the new Version to the … Read more

How to Fix “Something Went Wrong” Error in Office 365
How to Fix “Something Went Wrong” Error in Office 365 In this guide, we’ll break down the most common causes for the frustrating “Something went wrong” error when trying to sign in … Read more

How to Change Network From Public to Private
How to Change a Windows Computer Network Adapter from Public to Private using Settings App or PowerShell Command Line When setting up a Windows 11 computer, the network profile is an essential … Read more

Start a Support Session
LME Services Remote Access Download Download the support tool so LME can access your computer When you want to end the support session, be sure to quit the program. This ensures your … Read more

Write for US – IT Services, Technology, IT Support Guest Blog Posting
We at LME Services are excited to invite skilled writers and IT professionals to contribute to our platform. If you have a passion for information technology, problem-solving, creating insightful content, or have … Read more

Why Cyber Insurance is No Longer Optional: Protecting Your Business in the Digital Age
Why Cyber Insurance is No Longer Optional: Protecting Your Business in the Digital Age As any IT consulting firm can tell you, cyberattacks can bring devastation to a business. One breach, one … Read more




